PCI DSS 4.0 has evolved the Standard's internal vulnerability scan requirements and now calls for internal vulnerability scans to be performed via Authenticated Scanning.
This requirement is considered best practice until March 31st, 2025 after which it must be fully implemented for an entity that is maintaining compliance with PCI DSS and if the specific control for internal vulnerability scanning applies to their environment.
Why authenticated scans and why now?
A mature vulnerability management program has always been a cornerstone for an entity that wants to maintain a cybersecurity program and/or is subject to various regulations. The standard already has controls that say that security patches with a severity of high or critical need to be applied within 30 days. The vulnerability scan is a test/control to perform a follow-up to ensure it's done.
What is an unauthenticated scan?
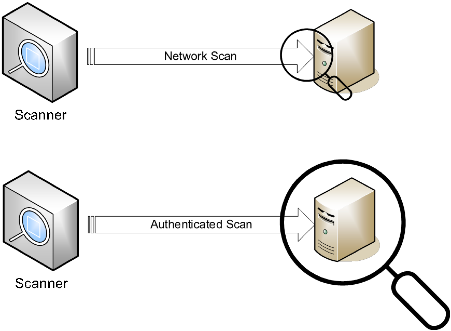
An unauthenticated network scan tests systems that are offer services to the network, such as a web server or application service, for vulnerabilities based on the responses provided by the service. The limitation with these network-based scans only is that they can only detect vulnerabilities on systems that have ports open (visible on the network). The scans can detect the version of system/software behind the open ports and compare it to a vulnerability database. If software is installed that doesn't have open ports, for example, an office productivity application, vulnerabilities will most likely not be detected but could still exist. An attacker could still exploit those vulnerabilities, for example, if the user was manipulated into opening a malicious attachment sent in a phishing email. Unauthenticated scanning can be considered an outside in view of the system vulnerabilities.
What is an authenticated scan?
An authenticated scan works by using account credentials and logging on to the system remotely or by running an agent on the system. Using this method, the scanner has access to internal resources, such as registries and package versions, and is able to see the conditions of all applications and services on the system. An authenticated scan can detect vulnerabilities of all types affecting installed software, applications and libraries and does not rely on open ports or network visibility. Authenticated scanning can be considered an inside out view of system vulnerabilities.
To summarize, network-based vulnerability scans will detect based on open ports and an authenticated scan will be able to detect vulnerabilities on the full system.
An entity that moves from performing network-based vulnerability scans to authenticated scans is highly likely to experience an increased level of detected vulnerabilities and with that, an additional level of effort to remediate those vulnerabilities.
Feedback from entities that have either worked on an implementation of authenticated scanning or are planning to do so, is that they have seen or are anticipating a high level of detected vulnerabilities and this drives the effort and time it takes to handle the vulnerability management process.
PCI DSS 4.0 has also evolved the requirements for addressing identified vulnerabilities. The Standard still requires vulnerabilities ranked as high-risk or critical (per their vulnerability risk ranking) to be resolved but now includes a new requirement stating that vulnerabilities not ranked as high-risk or critical need to be addressed based on the risk defined in the entity's targeted risk analysis. This new requirement to address vulnerabilities based on risk exposure is also a best practice until March 31st, 2025, after which it must be fully implemented if applicable to the entity.
The combination of these two new requirements has the potential to create the perfect storm for many organizations:
- More vulnerabilities will be detected.
- A targeted Risk Analysis will be needed to determine allowable remediation periods for lower-ranked vulnerabilities (those not ranked high-risk or critical).
- All vulnerabilities will need to be addressed.
Implementation of authenticated scanning and a vulnerability management process that incorporates targeted risk analysis should be started sooner rather than later, depending on the maturity of your current vulnerability management process.
To ease implementation, many organizations will run authenticated scans in parallel with their usual unauthenticated scans and have a separate track of remediation for the authenticated scans results. This method minimizes any conflicts with or risks to ongoing PCI DSS compliance efforts.
Summary and next steps: Start the implementation process early due to an extended implementation timeline driven by the identification of more vulnerabilities and the need to address all of those vulnerabilities.
- Implement a solution that supports authenticated scanning
- Ensure credentials used for authenticated scans are managed in accordance with the applicable PCI DSS Requirement 7 & 8 controls
- Perform targeted risk analysis in order to ensure vulnerabilities that are not high or critical can be resolved based on the risk.
- Remediate vulnerabilities found and perform re-scans to confirm vulnerabilities are addressed.
References: Standard https://docs-prv.pcisecuritystandards.org/PCI%20DSS/Standard/PCI-DSS-v4_0.pdf

















































-program.png)















































