46 Ransomware Statistics and Trends Report 2026
Date published:
Dec 17, 2025

.svg)
46 Ransomware Statistics and Trends Report 2026
Ransomware remains a global crisis impacting all industries, with healthcare, manufacturing, education, and critical infrastructure sectors being affected the most. Evolving attack vectors, unpatched vulnerabilities, and supply chain attacks continue to drive costly downtime, data exfiltration, and recovery costs, even as average ransom payments decline.
Improved incident response, tested backups, and automated patch management have boosted data recoverability, but attack detection gaps and repeat attacks persist. Meanwhile, coordinated efforts by the FBI Internet Crime Complaint Center (IC3), FinCEN, Europol, and the International Counter Ransomware Initiative (CRI)—alongside campaigns like No More Ransom—are tightening oversight of cryptocurrency payments and disrupting major Ransomware-as-a-Service networks.
We’ve brought together 46 key ransomware statistics for 2026 that reveal:
• More than half of all ransomware attacks encrypt victims’ data.
• Ransomware payments are dropping, on average.
• Healthcare remains the industry most at-risk from ransomware.
• Ransomware is targeting small businesses more than enterprises (but all feel the negative effects).
Let’s explore our points in closer detail.
Scope, Definitions & Sources
A ransomware incident, according to the Cybersecurity and Infrastructure Security Agency (CISA) is an event where malware encrypts data on a computer or device to render it unusable.
In some cases, attackers apply multi-extortion tactics, where they may threaten to release sensitive data to the public, and even launch further attacks.
Our research and statistics are pulled from sources such as Verizon’s DBIR, Cybersecurity and Infrastructure Security Agency (CISA), Chainalysis, Espria, AHA, HHS, K-12 Dive, Comparitech, IBM and more. We predominantly cover the period from January 2024 to present, extending this scope where relevant.
Global Trends
Globally, ransomware is growing as the main cause of data breaches, with Virtual Private Networks (VPNs) and edge devices becoming major targets. However, encryption and payments appear to be dropping, overall. Ultimately, achieving PCI DSS compliance is just a small step towards protecting against increasingly sophisticated attacks.
Prevalence & Breach Share
1. Ransomware is present in around 44% of all data breaches, a dramatic increase of 12% year-on-year. 1
Initial Access & Exploited Vulnerabilities
2. Exploitation growth among edge devices and VPNs exploded by 22%, an eight-fold increase year-on-year. The median remediation time for the study’s edge vulnerability subset is around 32 days. 1
Encryption & Extortion Types
3. 50% of ransomware attacks led to data encryption, a drop of 20% year-on-year. What’s more, 28% of ransomware victims with data encryption experienced data theft, 14% of ransomware victims total. Around 6% of companies with encrypted data experienced extortion, doubling data year-on-year. 2
Payments & Negotiation Outcomes
4. Annual ransomware payments in 2024 reached $813.55 million, a drop from $1.25 billion in 2023. The largest median payment size per attack belongs to Dark Angels, who recovered $75 million in one lump sum. 3
Ransomware Attacks Stats by Industry
Below, we explore ransomware statistics across major affected industries, in particular healthcare, education, government and public sector, financial services and insurance,
manufacturing, retail and ecommerce, energy and utilities, technology, SaaS, and MSPs, and transportation and logistics.
Healthcare
Healthcare is the industry most at risk from cyberattacks, with downtime costs escalating, and vectors such as phishing and unpatched weaknesses looming large.
5. The healthcare industry experienced 238 ransomware threats in 2024, and was the most threatened industry, period, for the year. 4
6. Ransomware downtime costs healthcare companies an average of $1.9 million per day.5
7. Recurring initial access vectors for ransomware in the healthcare industry include phishing emails, unpatched vulnerabilities, remote desktop protocol attacks, and drive-by downloads. 6
Education (K–12 & Higher Ed)
Hundreds of thousands of student records are at risk from ransomware, yet many K-12 bodies haven’t invested in cybersecurity.
8. In 2024, there were 116 confirmed ransomware attacks launched on educational bodies, affecting 1.8 million records. 7
9. Educational bodies remain attractive to ransomware attackers thanks to the sensitive data they hold, and the fact 66% of K-12 districts have no specialist cybersecurity personnel. 8
10. Research suggests that common factors such as publicly disclosing vulnerabilities and running non-cloud technology can exacerbate data leakage in general across the sector. 9
Government & Public Sector (Federal, State/Local)
Official bodies are more at risk from ransomware than ever before, and costs from downtime alone are tipping $1 billion.
11. The first half of 2025 saw a 65% increase, year-on-year, in ransomware incidents affecting government bodies (totaling 208 attacks). 10
12. Between 2018 and 2024, 525 ransomware campaigns targeted U.S. government bodies. This resulted in losses of more than $1 billion in downtime. 11
13. Reasons behind ransomware attacks on U.S. government and public sector systems vary, from financial extortion, to theft of personal information, dark web data sales, to operational disruption. 12
Financial Services & Insurance
The financial industry is at increasing risk from ransomware, and software weaknesses (alongside IT/OT convergence) appear to be largely to blame.
14. Ransomware is affecting increasing numbers of financial organizations year-on-year, with 55% of companies worldwide impacted in 2022, to 64% in 2023, and 65% in 2024. 13
15. The most common routes of initial access for ransomware in financial services include weaknesses in APIs, poorly secured hardware, cloud misconfigurations, and convergences between IT and OT. 14
16. Despite cyber insurance claims falling year-on-year, ransomware losses are in fact increasing. 15
17. Insurance industry reports show that ransomware is now the predominant cause for large loss claims, overtaking general data breaches. 16
Manufacturing
Ransomware attackers are targeting manufacturing companies more than ever, and not just to hold data to ransom, but also to steal and leak. It is the most threatened industry, specifically, by ransomware.
18. Reports suggest that 80% of manufacturing companies experienced a year-on-year increase in general security issues, in line with IT and OT convergence. 17
19. Ransomware has cost businesses in the manufacturing industry more than $17 billion in downtime since 2018. 18
20. Ransomware attackers are targeting manufacturers for more than just money, with a landmark 43.9 million records compromised during 2023. 19
21. The manufacturing industry specifically experienced more ransomware attacks than any other industry in 2024. 20
Retail & eCommerce
Ransomware and cyberthreats in general are targeting retail and ecommerce to harvest credentials, and attacks appear to be worse during holiday periods.
22. Ransomware attacks on the retail industry doubled from the holiday season 2022 to 2023, with attacks spiking by up to 100% in the latter half of each year. 21
23. The retail sector was one of the worst affected by high-profile ransomware events in 2024, with an attack on CDK Global particularly increasing downtime. 22
24. Credential harvesting across all cybercrimes is now the number one threat vector for retail businesses. 23
Energy & Utilities (Critical Infrastructure / OT)
External threats remain big problems for mining and utility firms, with official agencies keen to impress the importance of avoiding obvious weaknesses.
25. In January 2025, the Cybersecurity and Infrastructure Security Agency (CISA) urgently advised critical infrastructure asset owners to secure themselves against rising threats targeting US oil and natural gas. 24
26. Ransomware attacks on utilities are surging by at least 42% year-on-year. 25
27. Top attack vectors for the mining and utilities sectors include system intrusion and social engineering. 94% of attacks on this sector in 2024 were external. 22
Technology, SaaS & MSPs
Our data shows that SaaS data is at increasing risk from ransomware right now – and that highly prominent attacks have done little to dispel the image that the industry is robust against malware. Ransomware supply chain threats continue to ravage the industry.
28. SaaS data is targeted by more than half of all ransomware attacks, and more than half of those were successful in penetrating enterprise data. 26
29. Prominent attacks on the supply chain that have caused downtime and data leakage over the past few years have included those impacting Kaseya, Accellion, and SolarWinds. 27
Transportation & Logistics
Research shows that attacks on this industry are predominantly financially-motivated, with ransomware taking a major slice of all cyberattacks.
30. Ransomware makes up 38% of all cyberattacks in the transportation industry, which have increased by 48% since 2020. 28
31. Almost two-thirds of ransomware attacks target essential supply chains for the sector. 28
32. The majority of cyberattacks affecting the transportation industry were financially motivated (98%). 22

Company Size Lens
Both small and large companies suffer with the aftermath of ransomware, however, attackers are focusing on smaller entities.
33. Over two-thirds of ransomware attacks between 2024-2025 targeted businesses with fewer than 500 personnel. 29
34. Ransomware accounts for 40% of SMBs’ disruptive cybersecurity incidents but incurs up to $50 million in recovery costs for enterprises. 30
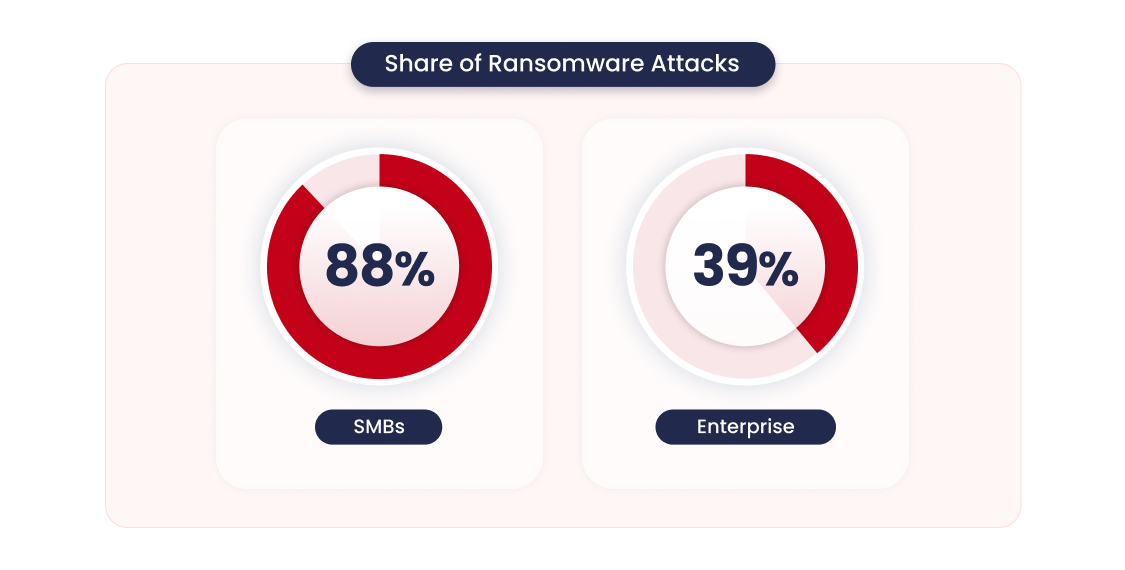
35. Ransomware makes up 39% of large company breaches, but makes up 88% of small business attacks. 22
36. Up to 60% of payers recovered some/all data after making a payment to a ransomware fraudster. 31
Regional View
Michigan is the U.S. state with the most ransomware attacks, and trends show this type of malware is taking a stranglehold across APAC and EMEA.
37. Calculating the attack rate by business numbers, Michigan has the most ransomware attacks in the U.S., however, New York, Florida, Texas, and California experience the most overall cyberattacks. 32
38. Across APAC, Thailand, Japan, Singapore, India, and the Philippines are the most-attacked countries. 33
39. Ransomware accounts for 40% of malware breaches in EMEA, with the region seeing malware in general accounting for more than half of the year’s data breaches. 22
Notable Ransomware Attacks and Case Studies
The past few years have seen a surge in advanced ransomware threat actors deploying business-style precision in their campaigns, often exploiting sophisticated attack vectors and leveraging double extortion tactics. From BlackCat’s attack on Change Healthcare to global incidents like the Costa Rica ransomware attacks (2022) and the dismantling of REvil and Hive, these cases reveal how deeply ransomware affects frontline IT and cybersecurity professionals.
40. In February 2024, BlackCat (ALPHV) encrypted systems at Change Healthcare, disrupting U.S. healthcare billing and prescription processing nationwide. The company reportedly paid $22 million in Bitcoin, but the attackers retained data and re-extorted through RansomHub affiliates. 40
41. A joint U.S.–U.K. law enforcement operation dismantled major LockBit infrastructure in early 2024, seizing decryption keys and charging five affiliates. LockBit had impacted more than 2,000 organizations worldwide, extracting over $120 million in ransoms. 35
42. Before being dismantled by the Department of Justice, Hive targeted 1,500+ victims in 80+ countries, extorting over $100 million. U.S. agents infiltrated the group’s servers and distributed decryption keys, preventing roughly $130 million in additional losses. 36

U.S Law Enforcement Response
Ransomware remains a top-tier national security and financial-stability threat in the U.S. Federal agencies are escalating enforcement, tracing illicit crypto flows, and improving victim reporting mechanisms. FBI data shows continued growth in incident reports, while FinCEN and Treasury actions highlight increasing scrutiny of cryptocurrency payments tied to ransomware.
43. Ransomware incidents reported to the FBI Internet Crime Complaint Center (IC3) rose by 9% year-on-year in 2024, reflecting growing severity and attention. 37
44. In 2024, the IC3 received 3,156 complaints identified specifically as ransomware attacks. 38
45. Up to 66% of ransomware-related payments reported in Suspicious Activity Reports (SARs) are made in Bitcoin (BTC); requests for Monero (XMR) (a more privacy-centric coin) are increasing. 39
Controls That Move the Needle
Despite their best efforts, middle-market firms continue to struggle to protect themselves against ransomware threats.
46. Only 41% of middle-market companies’ existing security defenses successfully blocked ransomware attacks in 2024. 40
Conclusion
As we head into 2026, ransomware continues to evolve through sophisticated attack vectors, data exfiltration, and Ransomware-as-a-Service (RaaS) models that amplify both scale and impact. While average ransom payments are declining, overall downtime costs, recovery expenses, and reputational harm keep rising—especially across healthcare, education, manufacturing, and other critical infrastructure sectors.
Organizations still face challenges with compromised backups, weak incident response, and repeat attacks, often fueled by unpatched vulnerabilities and supply chain risks. In response, agencies like the FBI IC3, Europol, FinCEN, and the International Counter-Ransomware Initiative (CRI) are tightening legal and regulatory pressure and disrupting cryptocurrency-based ransom payments. Strengthening defenses with AI-driven detection, automated patching, MFA, and tested backups remain critical for faster containment and long-term data recoverability.
There is no better time to revolutionize the way you protect your infrastructure, internal data, and customers against evolving threats. A great first step is to engage the help of experts at VikingCloud, such as through regular vulnerability scanning and penetration testing.
FAQs
The average total cost of a ransomware attack—including downtime, recovery, and reputational damage—ranges between $1.8 million and $5 million per incident in 2025. While ransom payments are declining, indirect costs like lost productivity, data restoration, and cybersecurity consulting continue to rise. Healthcare and manufacturing firms face the highest downtime expenses.
Attackers view SMBs as low-hanging fruit due to weaker cybersecurity defenses, outdated systems, and inconsistent patching practices. Many rely on third-party IT providers or lack dedicated security teams, making them more susceptible to Ransomware-as-a-Service (RaaS) operators looking for fast payouts.
Leading experts emphasize proactive defense and resilience over reactive measures. Key prevention steps include enabling multi-factor authentication (MFA) across all access points,automating patch management to close known vulnerabilities, regularly testing and segmenting backups to ensure recovery, deploying AI-based threat detection for early anomaly spotting, and conducting employee phishing simulations and training
Collaborative task forces like the International Counter Ransomware Initiative (CRI), Europol, and the FBI’s IC3 are working to disrupt ransomware ecosystems by tracking crypto transactions, infiltrating RaaS networks, and sharing intelligence across borders. Successful takedowns of groups like LockBit, Hive, and BlackCat (ALPHV) in 2024–2025 highlight growing international coordination.
Experts predict ransomware will evolve toward AI-assisted attacks, supply-chain infiltration, and data-leak extortion rather than encryption alone. Expect growth in zero-day exploit usage, deepfake-enabled social engineering, and targeting of cloud-based SaaS ecosystems. Meanwhile, increased regulation and mandatory reporting may reduce payment success rates but won’t eliminate threats entirely.
Sources
- Verizon
- Espria/Sophos
- Chain Analysis
- AHA
- Comparitech
- HHS
- Comparitech
- K-12 Dive
- NIH
- Industrial Cyber/Comparitech
- Comparitech
- IC3
- Statista
- Bobsguide
- The HIPAA Journal
- Risk & Insurance/AXA XL
- Manufacturing Digital
- Infosecurity Magazine
- ISS Source
- IBM
- Retail & Hospitality ISAC
- Verizon
- Security Magazine
- CISA
- Infosecurity Magazine
- Odaseva
- Pwc
- Rinnovabili
- Gray, Gray, & Gray LLP
- Cyentia
- Hiscox
- NordLocker
- ET Edge Insights
- IBM
- U.S Dept. of Justice
- U.S Dept. of Justice
- The HIPAA Journal
- FBI
- FinCEN
- RSM US



.png)