A Complete Guide to PCI Compliance
If you run a business that handles and processes debit or credit card information, it’s essential that you meet all 12 major requirements set by the Payment Card Industry Security Standards Council (PCI SSC).
Failure to meet PCI compliance can result in higher transaction fees and the loss of card processing privileges. Furthermore, non-compliance can lead to legal action and increased scrutiny from data regulators.
In this guide, we explore what PCI compliance means in practice, who needs to comply, what’s required, and the best practices you can put into action right away.
Understanding PCI Compliance
Understanding and adhering to PCI compliance on an ongoing basis helps to keep your business and customers safe from evolving cyberattacks.
However, according to Verizon, less than 50% manage to fully maintain compliance year on year, and the key to maintaining compliance is a robust PCI compliance program.
Organizations also need to understand the threat landscape and updates made to the PCI DSS to reduce risk with ever-evolving threats. For example, the most recent updates to the standard include protection against e-skimming. You can find more information in the “Exploring the New PCI DSS Requirements” eBook from VikingCloud.
PCI compliance is more critical than ever, considering 97% of U.S. top retailers have experienced third-party data breaches in the past year.
What is PCI DSS?
PCI DSS (Payment Card Industry Data Security Standard) compliance ensures that merchants keep the cardholder data they process as secure as possible against fraud and theft, such as in the event of a cyberattack.
It covers a series of payment security recommendations agreed upon by the card brands and is overseen by the PCI SSC.
What are the benefits of PCI DSS compliance?
Complying with PCI DSS helps reduce the risk of cyberattacks, data breaches, and associated costs while boosting customer confidence in your brand. It supports your overall risk management strategies and aligns with other compliance frameworks like NIST and GDPR.
Additionally, PCI DSS compliance streamlines business processes, improves vendor relationships, and ensures adherence to global standards set by card issuers.
Is PCI compliance a legal requirement?
Compliance is contractually enforced by major card brands and acquiring banks, meaning you’re at risk of fines and higher transaction costs if you don’t comply. You are not legally required to be PCI compliant, and it’s not enforced by government agencies or the PCI SSC.
However, non-compliant companies risk civil legal action if card data is leaked and may come under greater scrutiny from data regulators – for example, those ensuring firms adhere to CCPA, GDPR, and HIPAA.
Which parties are involved in PCI compliance?
Parties involved in compliance include card brands and networks such as Mastercard, Visa, JCB International, and American Express, and payment gateway and handling services such as PayPal, Stripe, and Square.
The parties involved with your compliance depend entirely on who you process payments with. Therefore, we always recommend that our customers check the compliance rules and standards set by the networks they trade with.
Who Needs to Comply with PCI DSS?
If your business uses any card service, you’ll need to comply with PCI DSS. This includes operators such as merchants, payment processors, banks, card issuers, software developers, and third parties that facilitate card payments.
The PCI DSS also applies to companies within these remits, regardless of size or payment channels.
Most importantly, PCI DSS also applies if you don’t store data from cardholders after processing—merely handling and processing, or having the ability to impact the security of this information, is enough to warrant compliance.
What are the PCI Compliance Levels?
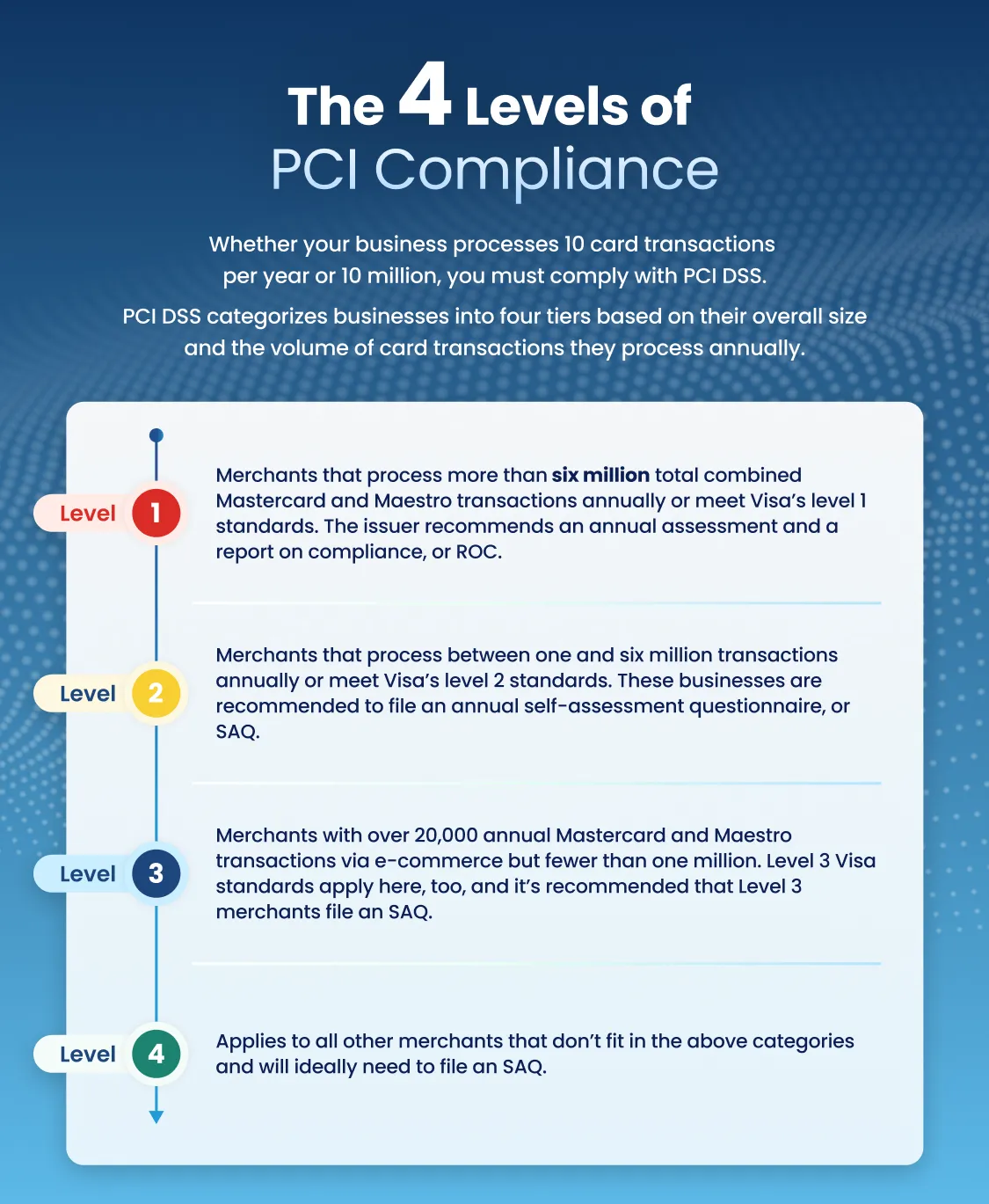
Whether your business processes 10 card transactions per year or 10 million, you must comply with the Payment Card Industry Data Security Standard (PCI DSS).
The more card transactions you process, the greater the risk of potential data breaches and security incidents. To help address this, PCI DSS categorizes businesses into four tiers based on their overall size and the volume of card transactions they process annually.
All merchants storing, processing, or transmitting cardholder data must be PCI-compliant. Compliance levels vary depending on the card issuer and processor involved. As an example, we’ve put together a quick summary of Mastercard’s levels for merchants:
- Level 1: Merchants that process more than six million total combined Mastercard and Maestro transactions annually or meet Visa’s level 1 standards. The issuer recommends an annual assessment and a report on compliance, or ROC.
- Level 2: Merchants that process between one and six million transactions annually or meet Visa’s level 2 standards. These businesses are recommended to file an annual self-assessment questionnaire, or SAQ.
- Level 3: Merchants with over 20,000 annual Mastercard and Maestro transactions via e-commerce but fewer than one million. Level 3 Visa standards apply here, too, and it’s recommended that Level 3 merchants file an SAQ.
- Level 4: Applies to all other merchants that don’t fit in the above categories and will ideally need to file an SAQ.
Mastercard recommends that businesses contact their acquiring banks to ensure they confirm their merchant levels. More information is available directly through Mastercard.
Of course, if your company doesn’t use Mastercard, you will need to consult the rules set by Visa, Square, JCB, or others as applicable.
PCI DSS v3 Compliance Requirements
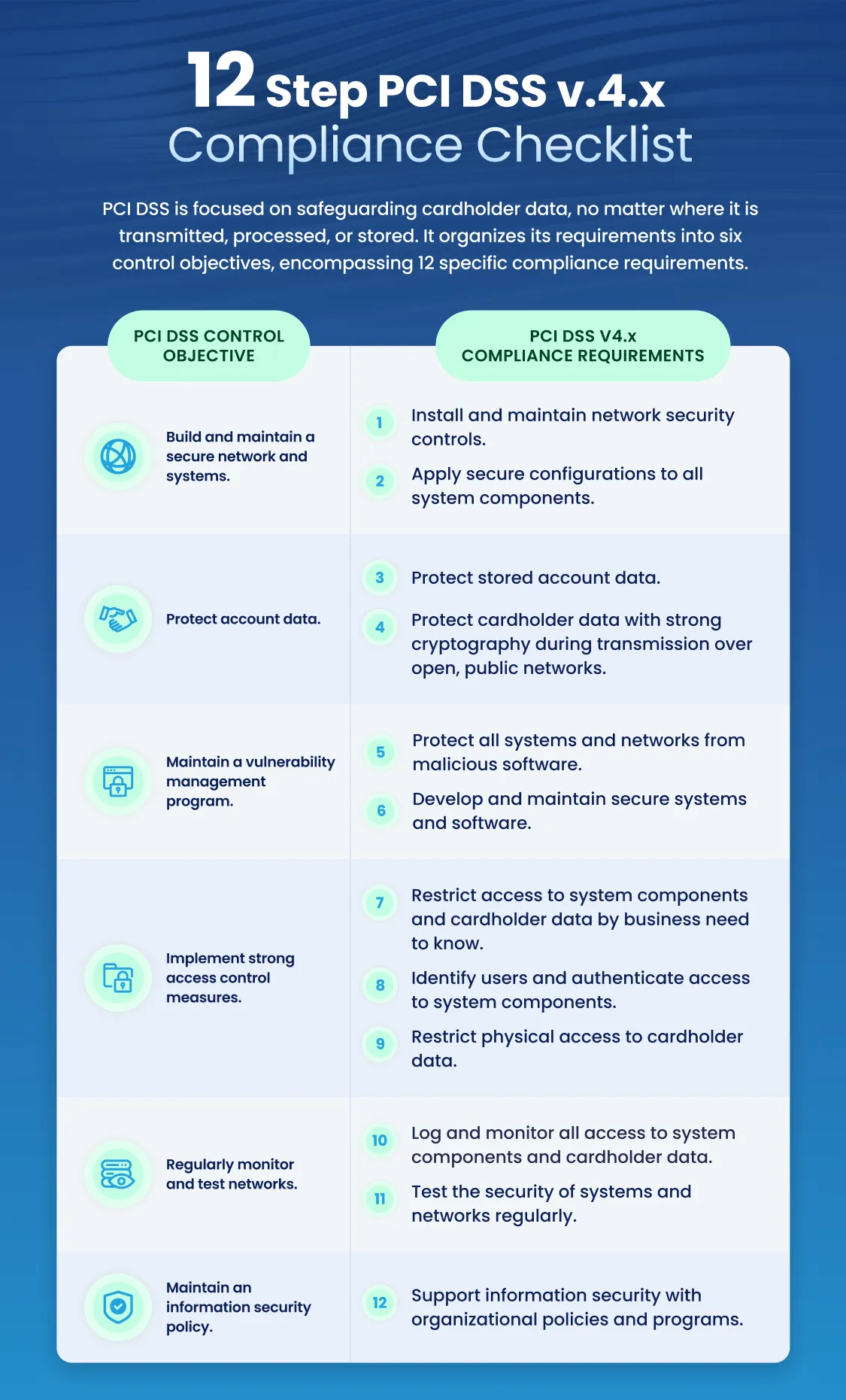
PCI DSS is focused on safeguarding cardholder data, no matter where it is transmitted, processed, or stored. It organizes its requirements into six control objectives, encompassing 12 specific compliance requirements.
The Six PCI DSS Control Objectives Are:
- Build and Maintain a Secure Network and Systems
- Protect Account Data
- Establish a Vulnerability Management Program
- Implement Strong Access Control Measures
- Regularly Monitor and Test Networks
- Maintain an Information Security Policy
Under PCI DSS, the six primary objectives are further broken down into 12 compliance requirements. These objectives and requirements cover network security, account data protection, vulnerability management, access control and user authentication, system protection and security maintenance, training and policy setting, security testing, and physical safeguarding.
These standards apply to any business that processes, stores, or transmits credit card information, regardless of size or transaction volume. VikingCloud helps our customers manage and protect their data across all 12 requirements.
Let’s explore the 12 compliance requirements defined by PCI SSC and an example strategy for staying compliant at each step.
1. Install and Maintain Network Security Controls
Install a functional firewall to protect against cyberattacks, and to continually test network connections for vulnerabilities. Processes such as penetration testing can help to find network weaknesses.
2. Apply Secure Configurations to All System Components
Regularly change passwords and amend user access controls, reducing functionality, and apply secure configurations as and where needed. Change password settings across networked devices and internal portals.
3. Protect Stored Account Data
Take steps to encrypt and securely store account data, including cardholder data, to protect it against both internal and external threats. Limit storage options, vet cloud storage vendors, and physically protect any on-site storage.
4. Protect Cardholder Data with Strong Cryptography During Transmission Over Open, Public Networks
Apply TLS 1.1 or higher encryption to websites and web applications, and follow data encryption and truncation methods to make cardholder data unusable if transferred. Avoid sending complete card data through channels such as email or IM, where hackers can intercept it.
5. Protect All Systems and Networks from Malicious Software
Install, run, and regularly update antivirus and anti-malware protection, and consult professional vulnerability scanning services.
6. Develop and Maintain Secure Systems and Software
Develop clear processes and policies to regularly update, check, and maintain system security across your entire infrastructure. Ensure that mobile and web applications are developed securely and protected as needed.
7. Restrict Access to System Components and Cardholder Data by Business Need to Know
Store cardholder data only when necessary, and if this is the case, restrict access to personnel who require this information.
8. Identify Users and Authenticate Access to System Components
Implement multi-factor authentication, biometrics, and even AI access controls to double up on ID checks – don’t just use simple passwords.
9. Restrict Physical Access to Cardholder Data
Store data securely in physical storage, implement multi-factor authentication, and install security monitoring equipment. In retail environments, secure and monitor POIs (Terminals) to detect tampering.
10. Log and Monitor All Access to System Components and Cardholder Data
Maintain thorough login audits, track user behavior, and regularly review access logs for signs of unauthorized access to cardholder data.
11. Test the Security of Systems and Networks Regularly
Regularly scan and test for vulnerabilities externally using an Approved Scanning Vendor and internally using authenticated scans. Perform penetration tests, monitor traffic that can access sensitive data, update and test IoT devices, and upgrade equipment wherever necessary.
12. Support Information Security with Organizational Policies and Programs
Establish a clear set of security policies that employees can follow and implement. Refresh these policies regularly and provide top-up staff training on the latest threats. Ensure that you manage your third-party service providers. Establish an incident response plan.
How to Become PCI Compliant
Becoming PCI compliant can be a complex process. It usually involves assessing your current security posture, implementing necessary controls, and then validating and maintaining your new posture in line with compliance requirements.
Here are some more details on how to ensure PCI compliance for small businesses:
- Assess your current security posture: Run a thorough audit of your security policies and processes, and build an inventory of your systems, access controls, and any data stored. Lay out your infrastructure as a top-down view. As part of your assessment, it’s best practice to create a cardholder data flow diagram that outlines where card data enters, moves through, and exits your environment. This helps identify vulnerabilities and scope.
- Implement required security controls: Carefully look through the security controls at each point where card data is likely to be accessed and consult the 12 requirements set by PCI DSS. Work with cybersecurity experts to upgrade systems, run scans, and update policies.
- Validate and maintain compliance: Enlist the support of a Qualified Security Assessor (QSA) to validate your compliance with PCI DSS and follow their recommendations to keep compliant for the years to come.
Challenges & Costs of PCI Compliance
PCI compliance service costs vary depending on the payment partners you work with, the size of your organization, and the cybersecurity professionals you enlist. It could cost you anywhere between hundreds of dollars and six-figure sums to keep compliant.
What’s more, laying out your infrastructure and carefully analyzing your current security controls can take considerable time and effort with professional support.
However, non-compliance can be much more expensive – and damaging – in the long run. You could lose money through:
- Penalties from service providers
- Losing business due to reputational damage
- Legal costs through customer/vendor lawsuits
- Insurance claims made against you
- Client and account loss and cancellation
- Penalties associated with data protection regulations (e.g., GDPR)
- Penalties applied by card industry partners
We always encourage our customers to consider the costs of the worst-case scenario compared to the initial costs of cybersecurity and PCI compliance.
Best Practices for Maintaining PCI Compliance

Some of the best PCI compliance practices we recommend to our clients include following strong data security measures, updating training, using PCI-compliant processors, and storing data only when necessary.
We also suggest choosing systems and software that make compliance easy and that you update security policies regularly.
Here’s a deeper dive into these 5 best practices:
- Follow strong data security measures: Apply stringent access controls, regularly update passwords and software, and run regular vulnerability scans.
- Use PCI-compliant third parties: Use compliant processors such as those mentioned above – Square, Stripe, and more and ensure that all your third parties that touch cardholder data or can affect the security of cardholder data are compliant.
- Regularly update training and security policies: Ensure your team respects and understands how to safely handle, process, and store cardholder data.
- Avoid storing data unless necessary: The more data you store, the more compliance hoops you will need to leap through.
- Use systems that support easy compliance: For example, use professional software designed to support data protection frameworks.
What’s more, we always suggest that you use systems that PCI SSC recommends to avoid all doubt that you’re following the right processes. You should always seek assistance from cybersecurity professionals to scan, audit, and identify potential data risks.
PCI Compliance Resources
PCI compliance resources include the PCI SSC’s help center, your payment processor’s support team, self-assessment tools and SAQs, qualified QSAs, and cybersecurity experts.
Here’s a breakdown of where to go for help if you need it:
- Check out the PCI SSC’s resources center: PCI SSC’s merchant resources help business owners understand the potential impacts of poor cardholder data management and advise on the next steps to take to ensure compliance.
- Consult with your payment processor: Whether it’s Visa, Stripe, or any other processor, if you have any questions about PCI DSS, contact their support team. Remember to ask about compliance fees, if applicable, and any contractual obligations you have in place.
- Use self-assessment tools and SAQs to ensure compliance: If you’re unsure about your compliance requirements or whether you meet these standards, utilize SAQs provided by the PCI SSC.
- Consult with cybersecurity specialists: Protect your data using experts in the field, such as VikingCloud, to help you build stronger security and scan for vulnerabilities, ensuring you meet all the necessary requirements.
- Hire a QSA: Hiring a QSA trained and specialized in PCI DSS can help you assess your current posture and make recommendations on how to improve.
Above all, remember that becoming PCI DSS compliant isn’t a one-off process. You should take steps to maintain your cardholder data privacy and security all year round, and VikingCloud is here to help.
To learn more about how we can help you secure your cardholder data and ensure you meet compliance demands, contact our team now for a free consultation.
PCI DISS Compliance FAQs
Does PCI DSS apply if I only accept cards by phone?
Yes, PCI DSS applies to any business that handles cardholder data. The method of acceptance doesn't change compliance requirements.
Do I still need to be PCI compliant if I use a third-party processor?
Yes, using a processor doesn’t exempt you from PCI DSS. While it may reduce exposure and reduce compliance efforts, ultimately, you’re still responsible for ensuring data is handled securely. It’s also your responsibility to verify that your processor is PCI compliant and to ensure your systems and processes comply with applicable requirements.
Do I need to validate PCI compliance for each business location?
If all locations use the same Tax ID, you typically validate once annually. However, quarterly scans by a PCI SSC Approved Scanning Vendor (ASV) may still be required for each location.
We only sell online. Which SAQ applies?
Service providers must typically complete SAQ D for Service Providers if they are eligible. This is the most comprehensive of the SAQs and applies to entities that process, store, or transmit cardholder data on behalf of other businesses. The correct SAQ depends on how your e-commerce site is structured. We advise our clients to learn more about this in our PCI SAQ 3.1 guide or contact us for the right fit.
We don’t store card data. Do we still need to be PCI compliant?
Yes, accepting cards in any form triggers PCI obligations. Not storing data reduces scope but doesn’t eliminate compliance. Ultimately, we advise our customers that PCI compliance is more straightforward but still required in these situations.
Are debit cards covered under PCI?
Yes, PCI DSS includes all credit, debit, and prepaid cards from major brands. This applies regardless of transaction type.
Is having an SSL certificate enough for PCI compliance?
No, SSL is only one part of the equation. Full PCI compliance involves broader security controls. We suggest exploring the information on level 4 merchant requirements in the guide above, ensuring a secure connection between the customer’s browser and the web server, as well as validation that the website operators are a legitimate, legally accountable organization.
Can I store credit card data?
We advise customers that it's often easier to avoid storing credit card information. However, those that set up recurring billing or other regular payments can use third-party vault and tokenization services to safely store data. Using a vault replaces sensitive card data with a secure token, enabling recurring billing without storing the data yourself. If you store card data internally, you face stricter PCI DSS requirements and may be required to undergo an on-site audit by a Qualified Security Assessor (QSA).
Note: Sensitive Authentication Data (such as CVV, PINs, and magnetic stripe data) must never be stored after authorization, even if encrypted. This is a strict PCI DSS violation.
What are the penalties for non-compliance?
Fines range from $5,000 to $100,000 per month at the discretion of the specific payment brand. Non-compliance can also result in higher fees or account termination. Banks often pass fines down to merchants, potentially leading to higher fees or terminated relationships. Though rarely publicized, these penalties can be devastating for small businesses. Review your merchant account agreement to understand your risk.
What is “cardholder data”?
Cardholder data includes the full Primary Account Number (PAN) alone or with name, expiration, or service code. Sensitive Authentication Data, which must also be protected, includes full magnetic stripe data, CAV2, CVC2, CVV2, CID, PINs, PIN blocks, and more.
What is the definition of a “merchant”?
Anyone accepting card payments for goods or services is a merchant. Some may also act as service providers, depending on their role. We suggest that you learn more about different merchant roles in our post here. The PCI SSC defines a merchant as any entity that accepts payment cards bearing the logos of Visa, Mastercard, American Express, Discover, or JCB for goods or services.
What is a “service provider”?
The PCI SSC defines a Service Provider as a:
“Business entity that is not a payment brand, directly involved in the processing, storage, or transmission of cardholder data. This also includes companies that provide services that control or could impact the security of cardholder data.”
The “merchant as a service provider” role is further specified as “a merchant that accepts payment cards as payment for goods and/or services…if the services sold result in storing, processing, or transmitting cardholder data on behalf of other merchants or service providers.” Learn more about how to achieve compliance as a Service Provider in our post.
What counts as a payment application?
The term payment application has a very broad meaning in PCI. Any software that stores, processes, or transmits card data qualifies. This includes POS systems and online shopping carts. Ultimately, we advise our clients that any piece of software designed to touch credit card data is considered a payment application.
What is SSF?
SSF refers to Secure Software Framework and includes both Secure Software Standard and Secure SLC standard. The secure software standard ensures payment apps support PCI compliance and avoids storing sensitive data. Vendors should follow it to keep their apps secure.
PCI SSC maintains a list of validated applications
Can I print full card numbers on receipts?
PCI DSS requires masking PAN when displayed—showing only the first six and last four digits. While full card numbers and expiry dates may be printed on receipts, stricter laws, such as the FACTA (Fair and Accurate Credit Transactions Act of 2003), take precedence. Merchants must also follow PCI DSS physical security rules for stored paper receipts.
What is a vulnerability scan?
A vulnerability scan is a non-intrusive, automated test of a merchant’s or service provider’s external-facing systems to identify security weaknesses. Performed by an Approved Scanning Vendor (ASV), it detects potential risks without installing software or disrupting services.
Is vulnerability scanning required?
If you store cardholder data post-authorization or qualify for certain SAQs, a quarterly passing scan by a PCI SSC Approved Scanning Vendor (ASV) is required. This applies to SAQ types A, A-EP, B-IP, C, D-Merchant, and D-Service Provider under PCI DSS v4.x.
How often must I scan?
You must complete a passing scan every 90 days. Results are submitted to your acquirer as proof of compliance.
What if my business refuses PCI compliance?
We recommend that all our clients maintain PCI compliance. PCI DSS is not a law, but a security standard created by major card brands (Visa, Mastercard, Discover, AMEX, JCB). Non-compliant merchants risk fines, audits, card replacement costs, and reputational damage if a breach occurs. Investing in PCI compliance upfront helps avoid these costly consequences.s
Am I at risk if I run my business from home?
Yes, home networks are common targets due to weaker security. Hackers often exploit unsecured systems and always-on connections.
What should I do if my business is breached?
Payment card data breaches can happen to businesses of any size—even though many are preventable. If your small or mid-sized business experiences a breach, there are trusted resources to guide your response:
- Department of Justice: Best Practices for Victim Response and Reporting of Cyber Incidents
- PCI Council: Responding to a Data Breach – A How-to Guide for Incident Management
Electronic Transactions Association (ETA): Steps Consumers Can Take After a Data Breach
Are breach notifications legally required?
Absolutely. California led the way with its 2003 data breach notification law, prompting nearly all other states to follow suit. As of April 12, 2017, 48 states, along with D.C., Guam, Puerto Rico, and the Virgin Islands, have laws requiring entities to notify individuals of breaches involving personally identifiable information.
Sources
Federal Trade Commission. (2003). Fair and Accurate Credit Transactions Act of 2003. Retrieved March 24, 2025, from https://www.ftc.gov/legal-library/browse/statutes/fair-accurate-credit-transactions-act-2003
General Data Protection Regulation (GDPR). (n.d.). Regulation (EU) 2016/679. from https://eurlex.europa.eu/eli/reg/2016/679/oj/eng
Health and Human Services (HHS). (n.d.). HIPAA privacy rule and compliance. Retrieved March 24, 2025, from https://www.hhs.gov/hipaa/for-professionals/privacy/laws-regulations/index.html
Mastercard. (n.d.). Site data protection – PCI for merchants. Retrieved March 24, 2025, from https://www.mastercard.us/en-us/business/overview/safety-and-security/security-recommendations/site-data-protection-PCI/merchants-need-to-know.html
Payment Card Industry Security Standards Council (PCI SSC). (n.d.-a). SAQ Instructions and Guidelines. https://docs-prv.pcisecuritystandards.org/SAQ%20(Assessment)/Instructions%20%26%20Guidance/SAQ-Instructions-Guidelines-PCI-DSS-v4-0-1-r1.pdf
Payment Card Industry Security Standards Council (PCI SSC). (n.d.-b). What merchants need to know. Retrieved March 24, 2025, from https://www.pcisecuritystandards.org/merchants/
Payment Card Industry Security Standards Council (PCI SSC). (n.d.-c). Secure Software Standard, from https://docs-prv.pcisecuritystandards.org/Software%20Security/Standard/PCI-Secure-Software-Standard-v1_2_1.pdf
Payment Card Industry Security Standards Council (PCI SSC). (n.d.-d). Approved Scanning Vendors. Retrieved March 24, 2025, from https://listings.pcisecuritystandards.org/assessors_and_solutions/approved_scanning_vendors
Payment Card Industry Security Standards Council (PCI SSC). (n.d.-e). Glossary – Service Provider. Retrieved March 24, 2025, from https://www.pcisecuritystandards.org/glossary/service-provider/
Payment Card Industry Security Standards Council (PCI SSC). (n.d.-f). Completing the self-assessment. Retrieved March 24, 2025, from https://listings.pcisecuritystandards.org/pci_security/completing_self_assessment
Payment Card Industry Security Standards Council (PCI SSC). (n.d.-g). Responding to a cardholder data breach. Retrieved March 24, 2025, from https://www.pcisecuritystandards.org/documents/Responding_to_a_Cardholder_Data_Breach.pdf
Payment Card Industry Security Standards Council (PCI SSC). (n.d.-h). Homepage. Retrieved March 24, 2025, from https://www.pcisecuritystandards.org/
State of California Department of Justice. (n.d.). California Consumer Privacy Act (CCPA). Retrieved March 24, 2025, from https://oag.ca.gov/privacy/ccpa
U.S. Department of Justice. (2015, April 29). Best practices for victim response and reporting of cyber incidents. Retrieved March 24, 2025, from https://www.justice.gov/sites/default/files/opa/speeches/attachments/2015/04/29/
criminal_division_guidance_on_best_practices_for_victim_response_and_reporting_cyber_incidents2.pdf
Verizon. (n.d.). 2024 Payment Security Report. Retrieved March 24, 2025, from https://www.verizon.com/business/reports/payment-security-report/
VikingCloud. (n.d.-a). Cybersecurity statistics. Retrieved March 24, 2025, from https://www.vikingcloud.com/blog/cybersecurity-statistics
VikingCloud. (n.d.-b). PCI compliance for small businesses. Retrieved March 24, 2025, from https://www.vikingcloud.com/compliance-risk/pci-compliance-for-small-businesses
VikingCloud. (n.d.-c). Secure payment solution. Retrieved March 24, 2025, from https://www.vikingcloud.com/compliance-risk/secure-payment-solution
VikingCloud. (n.d.-d). PCI compliance overview. Retrieved March 24, 2025, from https://www.vikingcloud.com/compliance-risk/pci-compliance
VikingCloud. (n.d.-e). Vulnerability scanning. Retrieved March 24, 2025, from https://www.vikingcloud.com/cybersecurity/vulnerability-scanning
VikingCloud. (n.d.-f). How does taking credit cards by phone work with PCI? Retrieved March 24, 2025, from https://www.vikingcloud.com/blog/how-does-taking-credit-cards-by-phone-work-with-pci
VikingCloud. (n.d.-g). PCI SAQ 3.1 e-commerce options explained. Retrieved March 24, 2025, from https://www.vikingcloud.com/blog/pci-saq-3-1-e-commerce-options-explained
VikingCloud. (n.d.-h). What is a PCI QSA? Retrieved March 24, 2025, from https://www.vikingcloud.com/blog/what-is-a-pci-qsa
VikingCloud. (n.d.-i). Merchant, service provider, or both? Retrieved March 24, 2025, from https://www.vikingcloud.com/blog/merchant-service-provider-or-both
VikingCloud. (n.d.-j). PCI compliance and the service provider. Retrieved March 24, 2025, from https://www.vikingcloud.com/blog/pci-compliance-and-the-service-provider
Electronic Transactions Association. (2023). Judge approves credit card swipe fee settlement. Retrieved March 24, 2025, from https://electran.org/eta-insight-judge-approves-credit-card-swipe-fee-settlement-2/

.svg)



.avif)